Not a week goes by without new malware threatening the billions of Android device users around the world. Among the latest dangers to date, we remember the BRATA malware; capable of spying on customer messages sent via their banking application.
This time, we owe the discovery of the day to computer security researchers at Cleafy. Indeed, these experts have detected the existence of a new malware called “Revive” . For now, the first cases have been in Spain around June 15; but everything indicates that the malware could spread quickly outside Spain's borders, in particular via phishing campaigns.
Unsurprisingly, the malware does not get its name by chance. It is even a direct reference to its main strength. Indeed, if the malware becomes inoperative, whether through the actions of the user or because of a bug, hackers are able to reactivate it remotely at their leisure. And to strengthen its hold on the infected device. As you will have understood, this makes “Revive” a particularly resistant malware and all the more harmful.
As a banking trojan, “Revive” currently targets users of BBVA (Banco Bilbao Vizcaya Argentaria), a multinational banking group based in Madrid and Bilbao. The operating mode is rather simple, since the hackers have opted for a classic phishing campaign.
Financial services users are the targets of the new Android banking malware "Revive"
Indeed, BBVA customers receive fake emails, SMS or messages by WhatsApp supposedly from the banking establishment. They are informed of the launch of a new application; and are invited to download it via a link outside the Play Store or App Store.
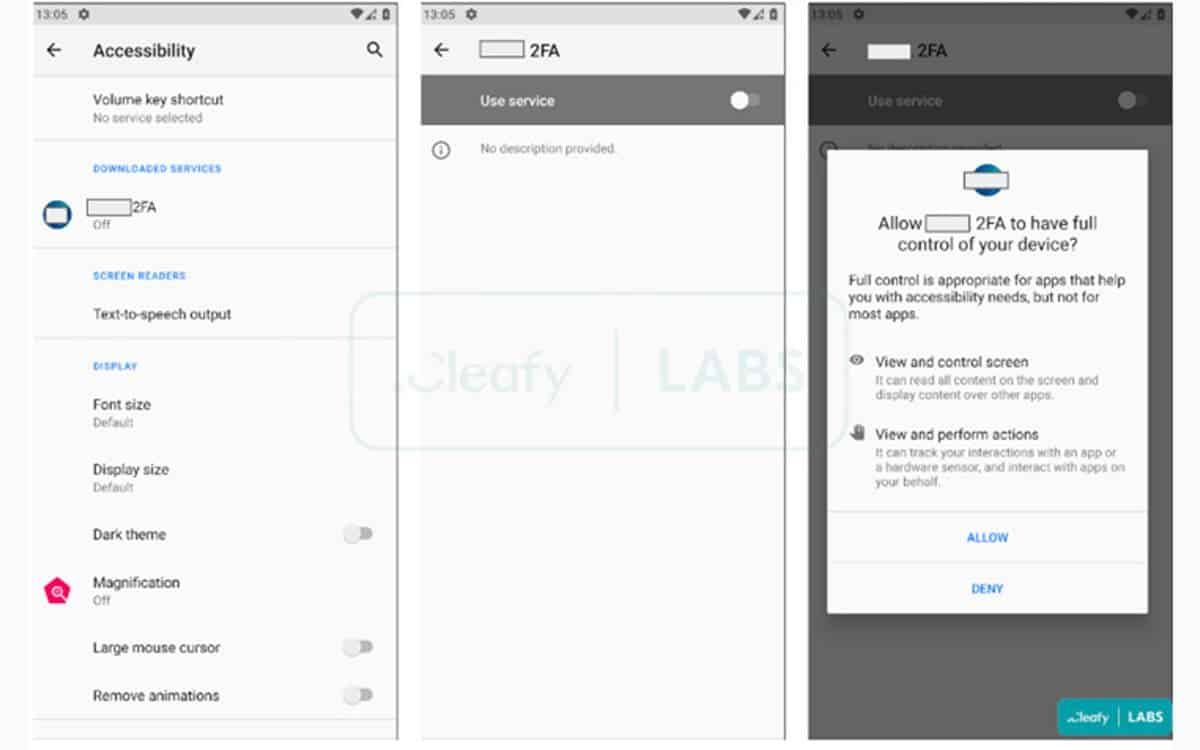
During installation, the program requires access to many features; such as being able to observe the touch commands performed on the screen; or even being able to access the microphone and the camera. In this way, the malware can scrutinize all the actions of the victim , including all installed applications.
Note also that “Revive” is able to capture the keystroke and intercept unique code SMS used as part of two-factor authentication. “ When the victim opens the malicious app for the 1st time, Revive asks the user to accept two permissions related to SMS and calls. After that, a clone of the targeted bank's login page appears, and if the user enters their credentials, they pass to the control server,” the researchers explain.
To protect yourself, the recommendation is simple: never agree to download an application, banking moreover, outside of a secure application store such as the Play Store or the App Store. Updating banking apps will still happen through these stores.






Place comments
0 Comments
You are currently seeing only the comments you are notified about, if you want to see all comments from this post, click the button below.
Show all comments